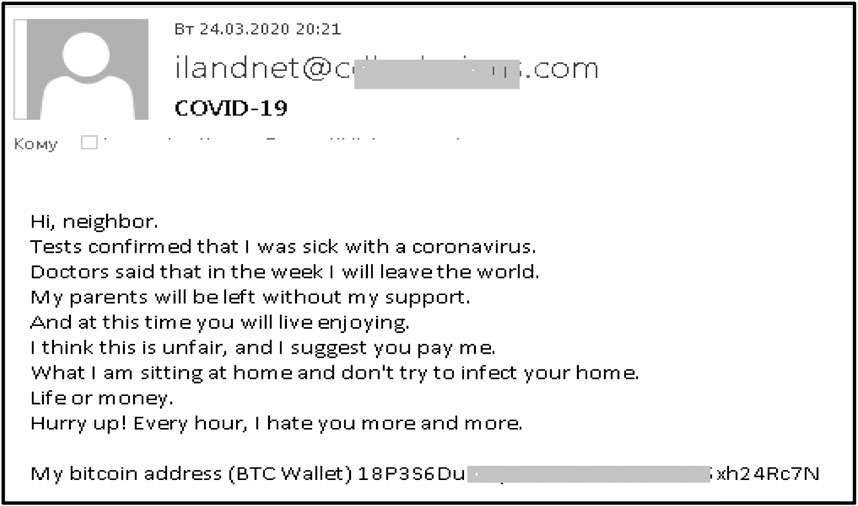
Lights, Camera, HACKED! An insight into the world of popular IP Cameras | NCC Group Research Blog | Making the world safer and more secure
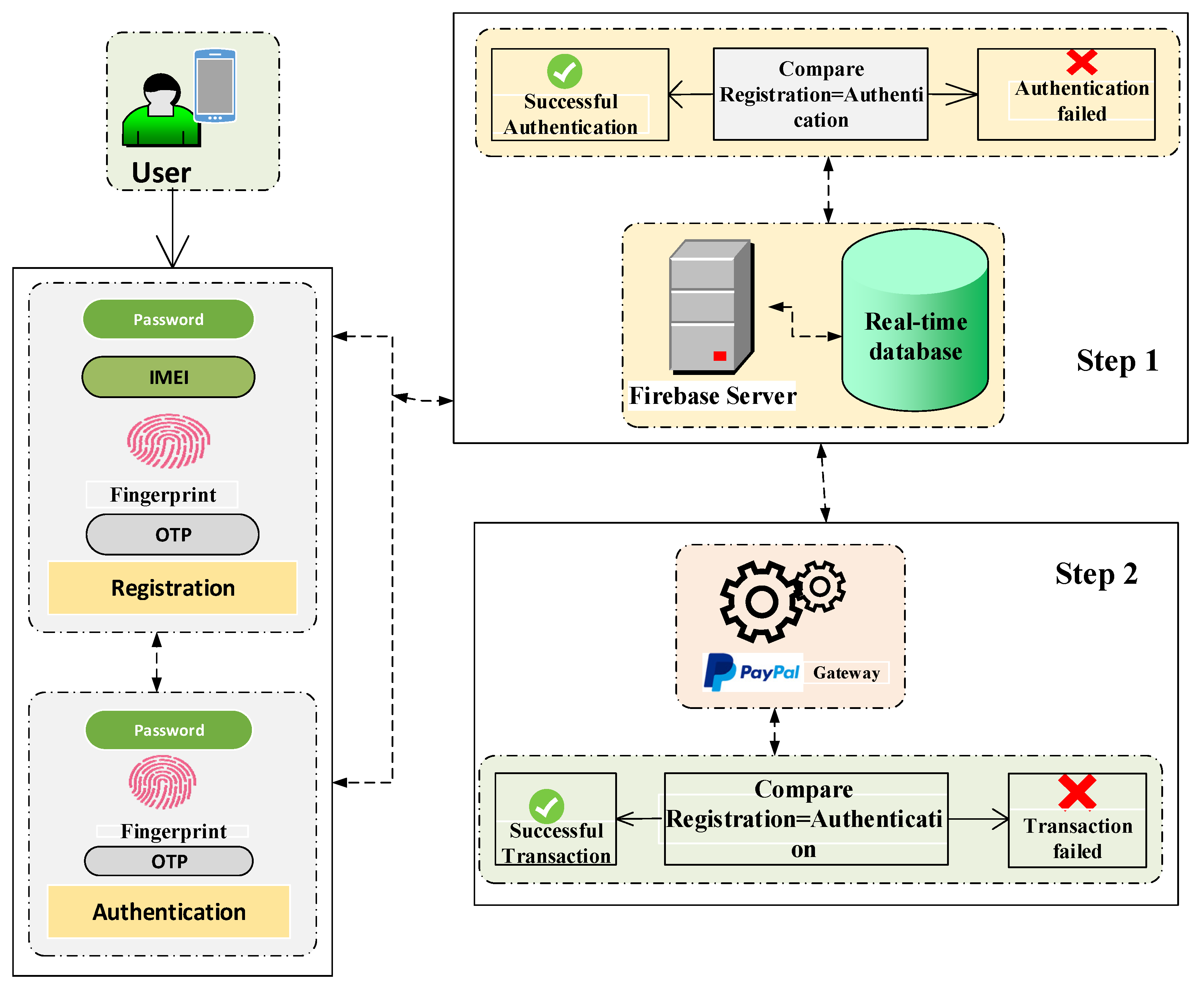
Electronics | Free Full-Text | Device Identity-Based User Authentication on Electronic Payment System for Secure E-Wallet Apps

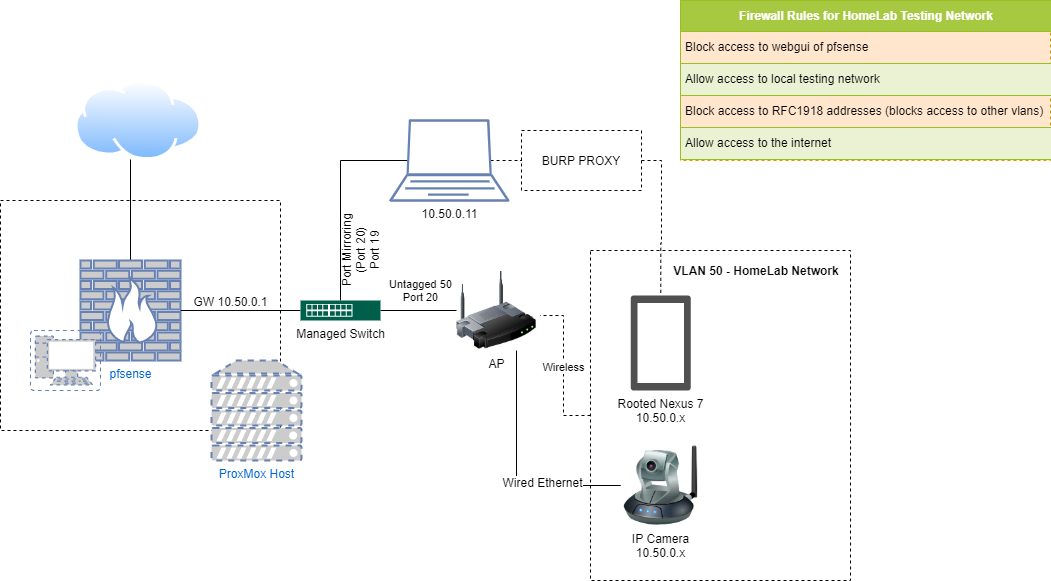
Exposed Video Streams: How Hackers Abuse Surveillance Cameras - Noticias de seguridad - Trend Micro ES